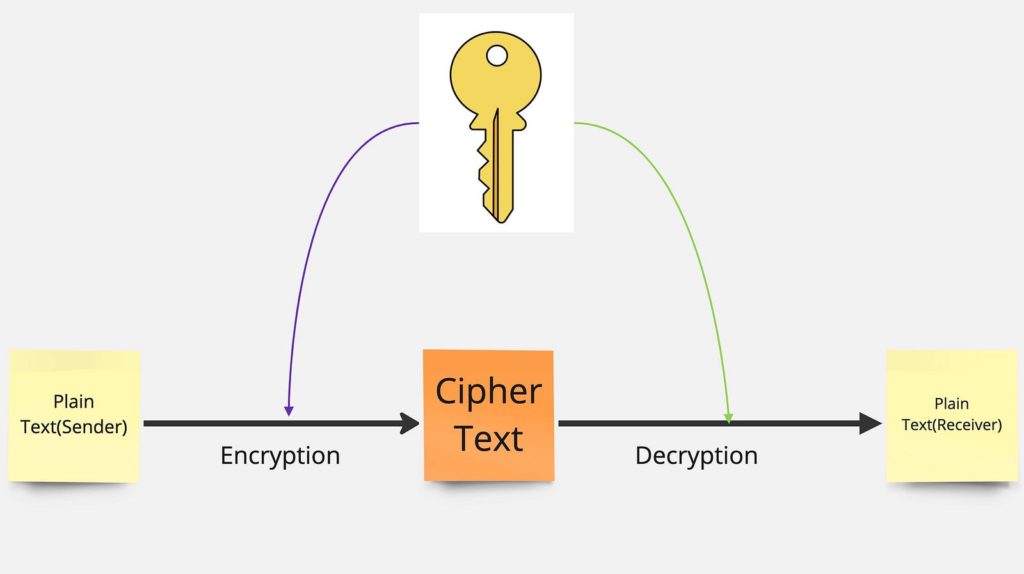
Ever wonder how secret codes work? It’s like having a super cool digital key to keep your messages safe. Let’s go on an adventure into the world of secure messages, where we’ll explore how digital locks, called encryption and decryption, make sure your secrets stay super safe!
Example: The Secret Locker Code
Consider a scenario where valuable items are secured using the principles of encryption and decryption.
- Encryption — Safeguarding Sensitive Information:
- Original Information: Imagine a piece of sensitive information, known only to you.
- Encrypted Data: To shield this precious data, encryption is employed. Using a unique algorithm (the key), the original information transforms into an encrypted version — a series of seemingly random characters guarding against unauthorized access.
2. Decryption — Accessing the Secured Information:
- Sharing Securely: To grant access, you share the encrypted data and the means to decrypt it — the key — with a trusted recipient.
- Decoding the Information: Empowered with the key, the recipient decrypts the data, unveiling the original content. Now, they can access the sensitive information securely.
In the cool world of cryptography, think of encryption like a superhero shield for your digital secrets. It keeps your important stuff safe when you send it. And guess what? Decryption, with the help of a special key, is like giving the right people the superpower to read the secret message. This shows how cryptography is the superhero keeping our digital secrets safe and sound!
Types of Cryptographic Techniques:
- Symmetric Encryption: The Shared Secret
Imagine you and your friend have the same secret language or code to talk to each other. Symmetric encryption is like that — it uses the same key for both encrypting and decrypting the message.
- Real-Life Example: Sharing a secret word with a friend and using it to talk in code.
2. Asymmetric Encryption: Two Keys for Added Security
Imagine you have a treasure chest and a special key. This treasure chest can lock messages, but only your secret key can open and read them.
- Real-Life Example:
Let’s say your friend wants to share a secret joke with you. They use the treasure chest to lock up the joke because everyone knows how to use it. The fun part is that only you, with your special key, can open and read the secret joke inside. It’s like having a magic treasure chest where your friend can hide jokes for you, and only you, with your special key, can unlock and enjoy the hidden surprises!
3. Hash Functions: One-Way Street
Hash functions are like a magic blender for information. You toss in your message, and out comes a unique hash. But here’s the cool part — you can’t turn the hash back into the original message.
- Real-Life Example: Turning your favorite snack recipe into a secret code that can’t be turned back into the recipe.
4. Public Key Infrastructure (PKI): Digital Signatures and Certificates
Imagine having a special stamp that only you and your friend recognize. PKI uses digital signatures and certificates to ensure the sender’s identity and the integrity of the message.
- Real-Life Example: Getting a letter with a seal that tells you who sent it and ensures it wasn’t tampered with.
5. Diffie-Hellman Key Exchange: Secret Handshake in the Digital World
Picture two friends creating a secret handshake that anyone can see but only they can understand. Diffie-Hellman Key Exchange lets two parties agree on a shared secret over an insecure channel without anyone else knowing what it is.
- Real-Life Example: Sharing secret plans in a crowded room, knowing that only the intended recipient can understand.
6. Quantum Cryptography: Next-Level Security with Quantum Bits
Quantum cryptography uses the fascinating world of quantum bits (qubits) to create super secure keys. It’s like having magical keys that change if someone tries to sneak a peek.
- Real-Life Example: Using quantum magic to send secret messages that are almost impossible to intercept.
| Technique | Description | Real-Life Example |
|---|---|---|
| Symmetric Encryption | Uses the same key for both encrypting and decrypting. | Sharing a secret word with a friend and using it to talk in code. |
| Asymmetric Encryption | Uses a pair of keys – one for encryption and a different one for decryption. | Your friend shares a secret joke using a treasure chest, and only you with your special key can open and read it. |
| Hash Functions | Turns a message into a unique code that can’t be turned back into the original. | Turning your favorite snack recipe into a secret code that can’t be turned back into the recipe. |
| PKI (Digital Signatures) | Ensures the sender’s identity and the integrity of the message. | Getting a letter with a seal that tells you who sent it and ensures it wasn’t tampered with. |
| Diffie-Hellman Key Exchange | Lets two parties agree on a shared secret over an insecure channel without anyone else knowing. | Sharing secret plans in a crowded room, knowing that only the intended recipient can understand. |
| Quantum Cryptography | Uses quantum bits (qubits) to create super secure keys. | Using quantum magic to send secret messages that are almost impossible to intercept. |
In the enchanting realm of digital communication, cryptography emerges as the unsung hero, silently securing our messages and digital interactions. Through the artful use of encryption, decryption, and a variety of cryptographic techniques, we transform simple data into impenetrable codes, ensuring the confidentiality, integrity, and authenticity of our information.
As we explored the magic of symmetric and asymmetric encryption, the one-way street of hash functions, the trust-building digital signatures of PKI, the secret handshakes of Diffie-Hellman Key Exchange, and the quantum leaps of quantum cryptography, it becomes clear how cryptography acts as a digital guardian, preserving the sanctity of our online experiences.
In our interconnected world, where digital communication is the lifeblood of information exchange, the importance of cryptography cannot be overstated. It forms the backbone of secure online transactions, protects sensitive personal data, and allows us to communicate freely, knowing that our messages are shielded from prying eyes.
So, the next time you send a message, make an online purchase, or share a secret with a friend, remember the invisible cloak of cryptography that envelops your digital world, safeguarding your information and ensuring that your online experiences remain secure, trustworthy, and magical. In the ever-evolving landscape of technology, cryptography stands as a beacon of security, ensuring that our digital adventures unfold in the enchanted kingdom of privacy and trust. 🏰🔐
Every time I visit your website, I’m greeted with thought-provoking content and impeccable writing. You truly have a gift for articulating complex ideas in a clear and engaging manner.