TryHackMe CyberSecurity Offer -Complete rooms to win prizes! 2021 is new Challenge from the Cybersecurity Learning Platform.
TryHackme is celebrating the release of their new Pre Security learning path , where its giving its readers a chance to participate in a competition to complete a room that’s part of the learning path and win tickets, get 3 of the same to redeem a prize.
If you’re a free user you can win 1 ticket, however subscribed users can win 2 tickets.
The ticket promotion ends on the 15th of July
| Lucky Title | Streak Freeze | 10% Swag Discount 0/50 Claimed | Stickers 0/300 Claimed | 1 Month THM Voucher Worth $10 0/30 Claimed | Swag Voucher Worth $20 0/15 Claimed | Throwback Voucher Worth $60 0/5 Claimed | 3 Month THM Voucher Worth $30 0/10 Claimed | Security+ Voucher Worth $275 0/2 Claimed | OSCP Voucher Worth $1000 Each 0/2 Claim |
Prizes
There is over $5,500 worth of prizes up for grabs! and you will be able to secure them by doing a maximum number of modules.
What is the Pre Security path?
Table of Contents
The Pre-Security learning path is a beginner-friendly & fun way to learn the basics.
Learn the pre-requisite technical knowledge to get started in cybersecurity. To attack or defend any technology, you to first learn how this technology works.

This learning process gives you the technical knowledge you need to get started with cybersecurity.
This learning path teaches mainly about how technology works and how different devices are connected and communicate with each other.
The learning path from Tryhackme provides a great start for all the learners from different backgrounds, be it a starter or an experienced professional.
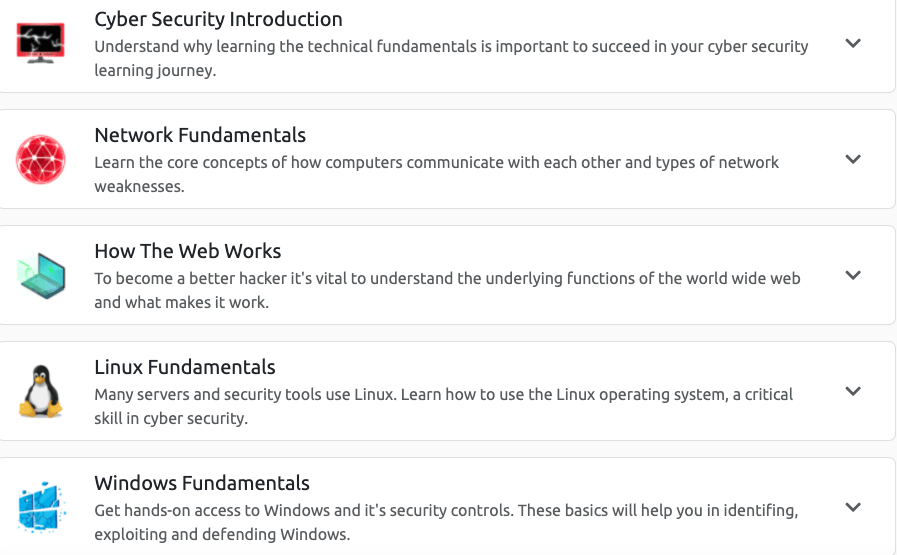
As seen above, the path offers a range of modules to learn from Introduction to cybersecurity to Fundamentals in Windows & Linux.
Module 1 –> Cybersecurity Introduction
This module provides a brief intro to web applications and Network Security with live examples through the attack box.
Attack box is a live environment created by TryHackme to learn cybersecurity in real-time
Here how to works:-
Source: TryHackMe
On TryHackMe you’ll learn by starting and hacking machines through your AttackBox, a web-based machine used to attack other machines you start on tasks.

- Click the blue
 button at the top of this room; the AttackBox is what you will use to access target machines you start on tasks such as this one.
button at the top of this room; the AttackBox is what you will use to access target machines you start on tasks such as this one. - Start the target machine shown on this task and wait 1 minute for it to configure.
- Copy the IP Address of the machine that you just started on this task, then on the AttackBox (right-hand side), open up Firefox (on the AttackBox) and paste the IP Address into the URL bar.

The machines you start on tasks (left hand-side) are the “target machines” and are accessed by the AttackBox (right hand-side).
Alternatively, you can access machines via OpenVPNWhen you’ve finished with a machine in any room, make sure to stop it by clicking the red “Terminate” button.
At the end of this module, we can understand the importance of security and vulnerable data can impact the users.
You will then be offered a guided path to step towards your cybersecurity career goal through learning paths.
Note: Although there are a lot of free modules to learn, we need a subscription to continue our learning in both the pre-security path and other learning paths.
You can get your subscription from here >> TryHackMe
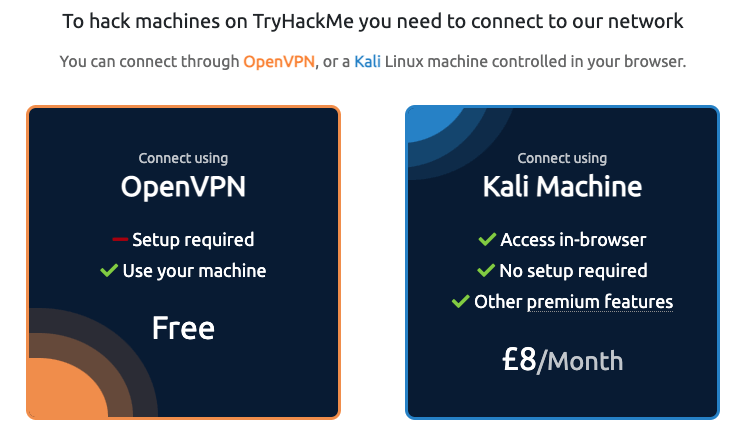
While doing modules, you will be able to redeem one more ticket for each module with a subscription to increase your chance of winning a prize.
Module 2–>Network Fundamentals
Before jumping onto how to protect the networks, one first needs to understand them and how they communicate via protocols, and how does the data transfer work?
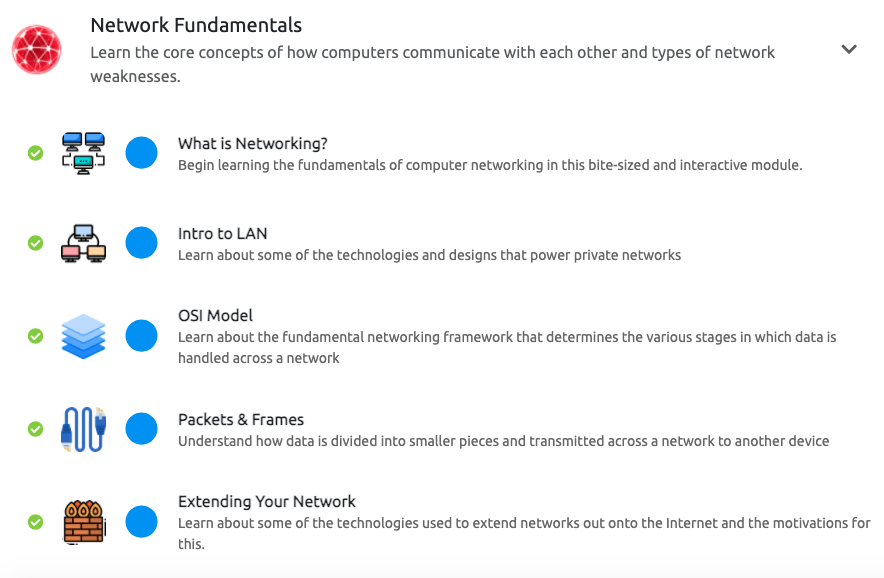
In a snippet, let’s see how these networks work…
How do the Networks work?
Computer networks use cables, fiber optics, or wireless signals to connect nodes such as computers, routers, and switches. Through these connections, devices on the network can communicate and share information and resources.
The network runs a protocol that defines how communication is sent and received. These protocols allow devices to communicate.
Each device on the network uses an Internet Protocol or IP address, which is a set of numbers that uniquely identifies the device and makes it visible to other devices.
A router is a virtual or physical device that facilitates communication between different networks. The router analyzes the information to determine the best way for the data to reach its final destination.
A switch connects devices, manages communication between nodes in a network, and ensures that bundles of information sent over a network reach their final destination.
The modules not only teach the basics to learn about networks but also helps to understand them via protocols and what these do at various layers.
Moving on to the OSI Model module, we will learn about the different layers involved in identifying network issues.
OSI model breaks down network communication into seven layers.
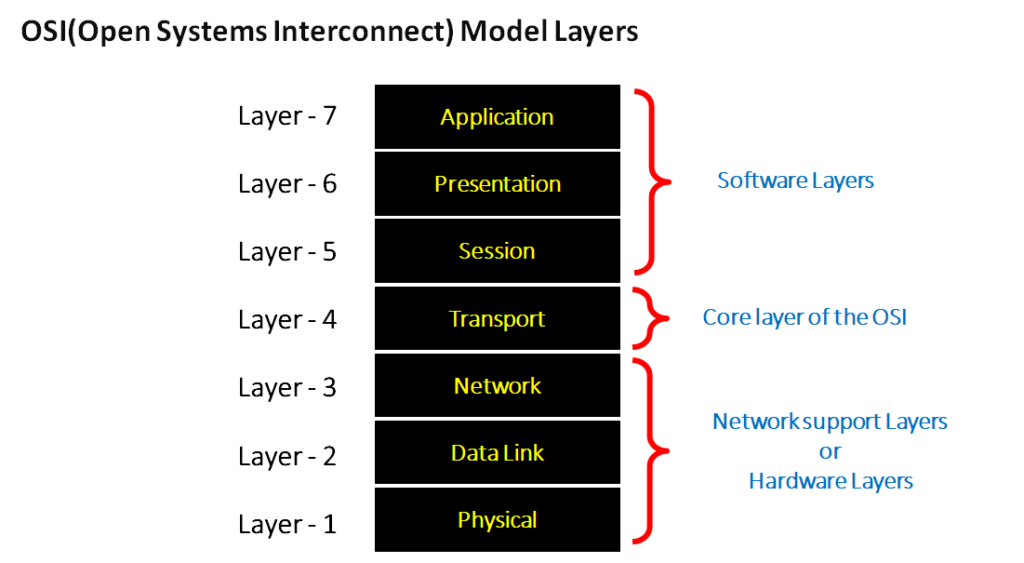
We further learn about TCP/IP & UDP protocols and the way they work. Furthermore, we investigate more about the communication differences in these protocols via real-time labs.
Overall, this module gives a strong foundation to those who want to learn more about networks and understand the way they talk to each other in a structured manner.
How the WEB Works?
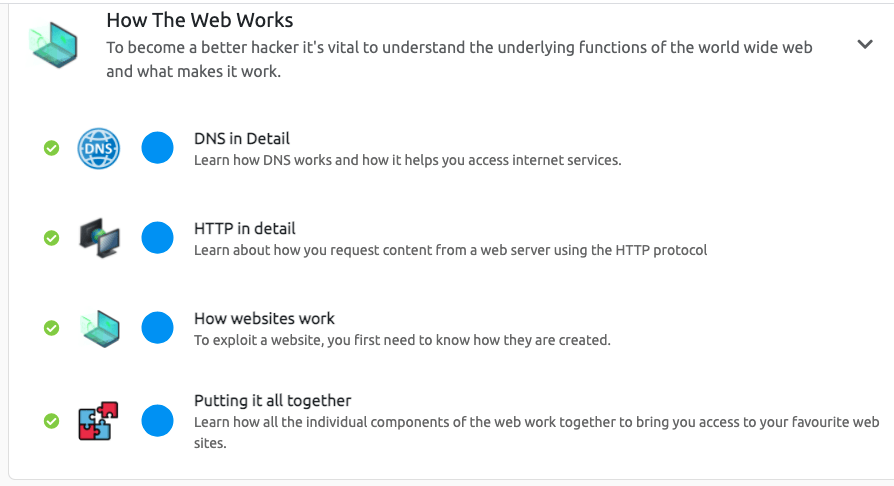
This module is all about the web as on Internet as a whole and how does it actually work?
The first topic in the module lets you know about the DNS and how does it work?
DNS-Domain Name System
This module comes with a live real-time example to help you understand the big picture of the DNS.
If you put it all together. The first step when querying for a domain name is that there is actually no root nameserver. Instead, the browser asks whether the domain’s DNS records are cached on the local resolving name servers. The nameservers that resolve are usually your Internet Service Provider (ISP), and popular websites like youtube.com may have records in their cache. In this case, the rest of the DNS lookup process is skipped.
However, these records are only retained for a short period of time. You have the option to set a TTL (Time to Live) each time you create a record. TTL indicates the period during which record information can be stored on the name server to be checked. The TTL is between 30 seconds and a week.
What if the record I’m looking for isn’t cached? The next name server to check is someone who has the authority to request and host records from the TLD’s root name server for that domain.
All these processes go behind in less than a blink to get the IPA address.
After that Module about HTTP -Hyper text transfer Protocol, will let you dive into about
- What is HTTP(S)?
- Requests And Responses
- HTTP Methods
- HTTP Status Codes
- Headers
- Cookies
- Making Requests with a live example
Module 3 will teach us about Websites and the technologies that are used and what vulnerabilities can we spot that makes a website vulnerable with a real time coding example.
Linux and Windows Fundamentals
These are the last modules in the learning path and is quite interesting to learn the technical stuff of scripting in the terminal, while learning more about the technicalities of the Windows Operating System.
Many cybersecurity tools are made by LINUX and it is one of the most important languages to learn inorder to excel in cybersecurity.
Learning about Windows provides a way of understanding the inner elements of the Disks and partitions while running an OS.
The Windows modules gives the learners a hands-on access to Windows, Configurations, Utilities and it’s security controls. These basics will help you in identifying, exploiting and defending Windows.
Linux Modules teaches the basic commands to get you started with using terminal and slowly moving to get into the necessary commands to manage the folders and the data inside them.
Overall, this path is great way to understand the basics of the Networks, Web and tools needed to start learning Cybersecurity.
