Describe securing network connectivity in Azure:-
Table of Contents
Describe Network Security Groups (NSG)
- The Network Security Group acts like a firewall that allows or denies the traffic from Different Network Interfaces.
- The NSG’s can be configured for Network interfaces, Subnets and virtual Machines in different tiers.
Describe Application Security Groups (ASG)
- The ASG increases the security in the virtual network environment by filtering traffic through pre-defined policies.
- These policies can be applied on virtual machines, workloads, applications etc along with provision of grouping resources and filtering traffic.
Describe User Defined Rules (UDR)
Role assignments are used to define the type of user and level of access to the resources.
The roles given are-
| Owner | Full control of resources along with management. |
| Reader | User can just view but cant do any changes |
| Contributor | Full control over everything except resource granting. |
| User Access Admin | Admin manages the users access to available resources. |
Describe Azure Firewall
- Network security service in the cloud environment that gives protection to the Azure resources.
- Offers built-in high availability & scalability.
- Azure has L3-L7 user configured firewall policies that offers protection from both HTTP/S attacks & non-http/s protocol attacks(ex:-Rdp,ssh etc).
- Describe Azure DDoS Protection
Describe core Azure Identity services:-
Describe the difference between authentication and authorization
| Authentication | The process of establishing the identity of a person |
| Authorization | The process of establishing the level of access the person has in the cloud environment. |
Describe Azure Active Directory
| Azure Active Directory | Identity and access Management Service |
Describe Azure Multi-Factor Authentication
| AMFA | Extra security feature to enable secure access to the services and systems. |
Describe security tools and features of Azure:-
Describe Azure Security Center
| Azure Security Centre | This is a monitoring service to prevent threats and gives protection to all Azure workloads along with the on-premise(On systems). Automatic Security assessments Offered in two tiers:- 1. Free Tier 2.Standard Tier |
Describe Azure Security Center usage scenarios
| Scenario 1 | Security Recommendations given by Azure security centre to enhance the security features |
| Scenario 2 | Incident Response :- The security centre identify the threats , perform assessments and do the investigation. |
Describe Key Vault
| Key Vault | The key vault is a place where user can store passwords, tokens etc with high security. Provides a Management solutions to securely store encryption keys, certificates(TLS/SSL) and Hardware security modules. |
Describe Azure Information Protection (AIP)
| AIP | Classification and protection of documents & emails by labelling . Labels:- Automatic-By Admin, Manual- Users and both types |
Describe Azure Advanced Threat Protection (ATP)
Azure Advanced threat protection is a service offered in Azure to identify and mitigate the threats.
The three components of ATP are:
| ATP Portal | Portal to monitor and manage malicious activities |
| ATP Sensors | The data presented in the portal is collected by sensors |
| ATP Service | Connected to Azure graph and get the reports on the Azure infrastructure |
Describe Azure governance methodologies:-
Describe policies and initiatives with Azure Policy
| Azure Policies | Workload standards can be defined, assigned and managed by the user. Policy is giving a set of rules to the resources, workloads etc. Scope to be created after policy creation and can be applied to the subscription . |
| Azure Initiatives | Grouping of policies to assign them various scopes . |
Describe Role-Based Access Control (RBAC)
| RBAC | Users will be given granular permissions depending on the role. |
| Owner | Full control of resources along with management. |
| Reader | User can just view but cant do any changes |
| Contributor | Full control over everything except resource granting. |
| User Access Admin | Admin manages the users access to available resources. |
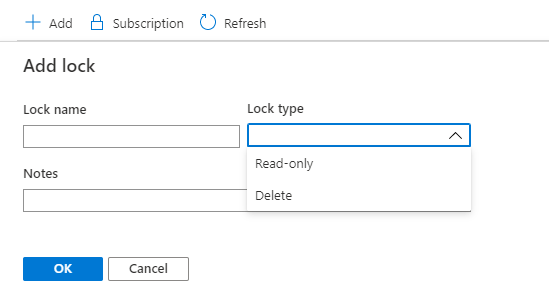
Describe Locks
| Locks | Resource locks are the settings that can applied to prevent changes accidentally. Resource Lock types are:- 1.Read-Only 2.Delete  |
Describe Azure Advisor security assistance
Advisor integrates with the security centre to bring of the recommendations to enhance the security of the cloud environment.
Describe Azure Blueprints
Azure Blueprints maintains a connection between the defined standards and the deployment of the resources.
Helps in auditing the deployment of the cloud resources.
Describe monitoring and reporting options in Azure:-
Describe Azure Monitor
| Azure Monitor | A service that enables user to collect the data from cloud and on-premise environments and analyse the data to find better solutions. |
Describe Azure Service Health
| Azure Service Health | This service allows users to track various azure services used in the regions and report on their health status. |
Describe the use cases and benefits of Azure Monitor and Azure Service Health
Use cases that make sue of the above services can be Azure containers, Virtual Machines etc.
Describe privacy, compliance and data protection standards in Azure:-
Describe industry compliance terms such as GDPR, ISO and NIST
| GDPR | Global data Protection Regulations European Union Law-Effective New rules applied to anyone who collects information from EU citizens |
| ISO | International Organisation for standardisation |
| NIST | National Institute of Standards and Technologies Standards and guidelines to manage cyber-security risks |
Describe the Microsoft Privacy Statement
This is the statement given by Microsoft on the how it handles the private data of the cloud users and the users of the applications associated with the azure resources .
Describe the Trust center
The trust centre provides the information on security appliance of Microsoft about their way to deal with privacy and Government regulations compliance all over the world.
Describe the Service Trust Portal
This is the website where Microsoft publishes its audit reports and compliance information in regards to it Cloud Services.
Describe Compliance Manager
This is a free tool hosted on STP.
This is workflow based risk assessment tool – to manage organisation compliance standards.
Determine if Azure is compliant for a business need
The Microsoft assists the users with how it follows all the standards and regulations according to the regions and the industries. It determines how it helps businesses to follow the guidelines according to the needs of the users.
Describe Azure Government cloud services
The Azure environment specially built for US government and defence department regions to meet their standards and regulations.
Describe Azure China cloud services
Offered in Partnership with the third party providers across china regions.
Click Here to move on to the next section

You have noted very interesting details! ps decent site.Raise your business
[…] Chapter Two […]